Polish industrial control systems (ICS/OT) continue to be targeted by Russian hacktivists, as evidenced by a recent attack on a hydroelectric power plant near Gdansk, as reported by CyberDefence24. This August attack involved manipulating operational parameters to disrupt the plant’s functionality, mirroring previous incidents that targeted critical infrastructure such as water and wastewater treatment plants, as well as pools and fountains. Concurrently, Polish authorities revealed the prevention of a cyberattack on a major city’s water supply, underscoring the increasing threat to national infrastructure. Furthermore, the Secret Blizzard hacker group, associated with Russian intelligence, has been actively deploying the ApolloShadow spyware to compromise devices used by diplomatic staff, highlighting the breadth of the Russian cyber campaign.
Read the original article here
Russian Hackers Attack Hydroelectric Power Plant in Poland
Well, it seems we’re talking about another instance of Russian cyber aggression, specifically targeting a hydroelectric power plant in Poland. It’s a situation that immediately raises alarms, especially given the context of ongoing geopolitical tensions. This isn’t just a technical issue; it’s a deliberate act of potential sabotage, aimed at disrupting critical infrastructure. And honestly, it feels like a familiar pattern at this point.
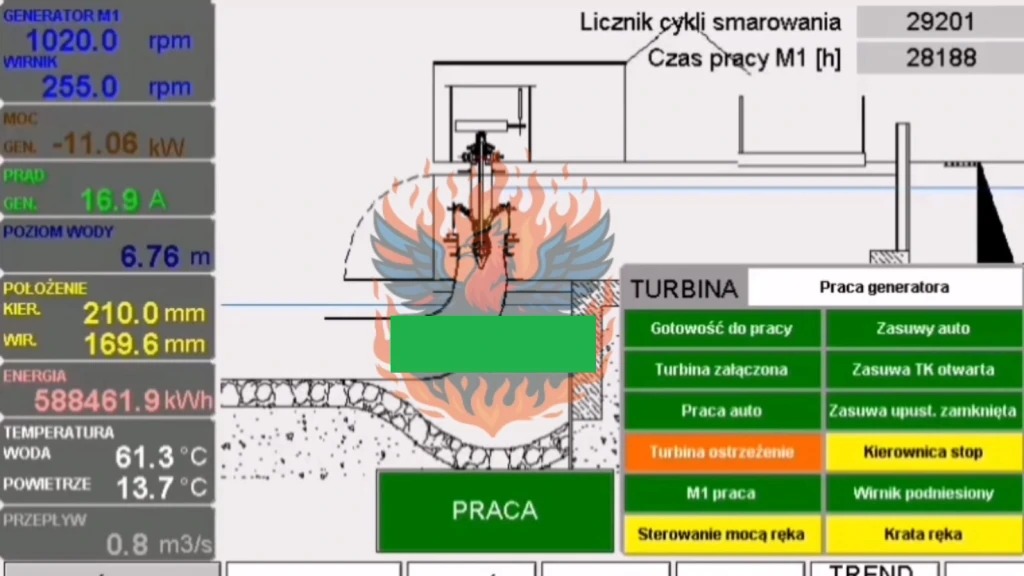
The reports coming out, courtesy of CyberDefence24, describe the attack as targeting a small hydroelectric plant in the Pomeranian Voivodeship, near Gdansk. Apparently, this isn’t a one-off either. The same power plant was attacked previously, and the hackers, or “hacktivists” as they’re sometimes euphemistically called, seem to be employing a consistent tactic. They’re manipulating operational parameters to either the minimum or maximum values. This, of course, causes the generator and rotor to shut down, which could lead to significant energy disruptions. It’s a simple yet effective strategy, highlighting the vulnerabilities of critical infrastructure.
This specific incident on the hydroelectric power plant, occurring in August, is just the latest in a series of attacks on Polish infrastructure, spanning the past few months. The reports include attacks on water treatment plants, both in April and May of 2025, as well as wastewater treatment plants in October 2024. The attacks seem broad, affecting the supply of resources and infrastructure, indicating a strategic approach to damage Poland’s infrastructure. I mean, we’re talking about vital services here – water, energy – things that directly impact people’s daily lives.
The fact that these attacks are often attributed to “pro-Russian hacktivists” is a bit unsettling, and it’s important to understand that these individuals are not simply activists. They are effectively engaging in acts of cyberterrorism, disrupting critical services. The term “hacktivist” feels like a way to soften the blow, to give a veneer of legitimacy to what is essentially malicious activity. They are, for lack of a better term, terrorists.
Furthermore, we’re talking about industrial control systems (ICS/OT) that manage critical infrastructure. The potential consequences of these attacks are very serious, potentially causing widespread disruptions in power or water supplies. The footage from August shows a clear manipulation of the plant’s parameters, raising alarm bells about energy security. It is also mentioned that Deputy Prime Minister of Poland reported on a separate attack on a water supply system in a major city, where authorities narrowly averted a complete cut-off of water access to the residents.
It is a concerning situation, particularly when considering the bigger picture. Russian-backed hackers are employing various tactics, including the use of sophisticated malware and targeted attacks. The news, for example, that the Russian hacker group Secret Blizzard, linked to the 16th FSB Center, has been infecting devices used by diplomatic staff with the ApolloShadow spyware is something to keep in mind. This spyware is designed to steal data, intercept communications, and gain persistent access to sensitive information. It’s a clear indication that these attacks are part of a wider strategy of espionage and sabotage.
This all begs the question, though: why are so many of these important infrastructures connected to the outside? The need for external communication may exist, but it needs to be separated from the main internal communications. This idea that anyone with an Ethernet cable can potentially connect to an extensive train network is scary. I mean, the infrastructure is old, but it also has vulnerabilities, and that’s a serious problem.
The question remains: what is the response when one country attacks the infrastructure of another? This brings the discussion to the question of NATO and Article 5, with the understanding that every country must decide how to react to any claims to provide aid independently. There are many opinions, but there is a general consensus: that the use of such a defense should never be taken lightly.
It appears many of these systems are accessible over the internet, making them incredibly vulnerable. This is concerning, especially when you think about the potential for widespread disruption. It’s clear that there are significant security vulnerabilities. The potential for an attack is a real threat, and the impact could be very serious.