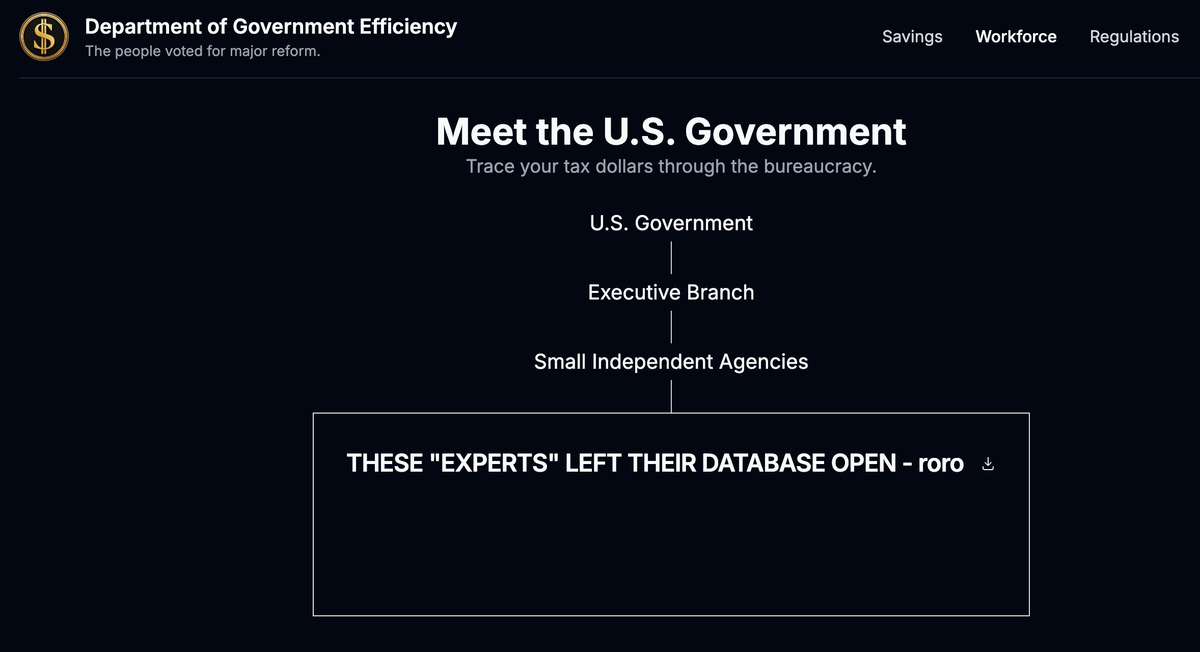
The hastily launched doge.gov website, intended to showcase Elon Musk’s government efficiency initiatives, suffers from a critical security vulnerability. Its database, accessible and editable by the public, has already been exploited, resulting in unauthorized entries appearing on the live site. This unsecured system, hosted on Cloudflare Pages rather than government servers, raises serious concerns about data integrity and the website’s overall reliability. The vulnerability highlights the risks associated with rapid deployment of government websites without adequate security measures.
Read the original article here
Anyone Can Push Updates to the DOGE.gov Website — “These ‘experts’ left their database open.” This situation is a truly remarkable example of cybersecurity negligence on a massive scale. The fact that individuals were able to directly modify a supposedly official government website’s database with such ease is deeply alarming. This isn’t a minor oversight; it’s a gaping hole exposing potentially sensitive government data.
The website, created ostensibly to track the federal government’s efficiency efforts, appears to be remarkably poorly secured. Reports indicate that it’s not even hosted on official government servers, raising immediate concerns about its legitimacy and security protocols. The choice to utilize a less secure, external hosting platform for such sensitive information points to a severe lack of due diligence and a significant disregard for basic cybersecurity best practices.
It seems the database powering the website’s information, supposedly about the federal workforce, is readily accessible and modifiable by anyone with sufficient technical knowledge. This means anyone, with malicious intent or simply for amusement, could alter the data displayed on the site. The potential for the spread of misinformation, data manipulation, and even more serious security breaches is staggering. The easily added entries, which included mocking comments about the website’s security, serve as a stark illustration of this vulnerability.
The fact that this vulnerability was discovered and exploited by independent individuals underscores the utter lack of robust security measures in place. The individuals involved apparently didn’t require sophisticated hacking techniques; rather, they found a fundamental flaw in the site’s architecture and exploited it. This highlights a significant failure in the website’s design, implementation, and testing phases. The ease with which these changes were made raises serious doubts about the competence and experience of those responsible for the website’s creation and maintenance.
The incident raises even broader questions about the overall cybersecurity posture of government agencies. If such a critical website can be so easily compromised, what does this suggest about the security of other, more sensitive government systems? The potential for far-reaching consequences, including data breaches, identity theft, and the compromise of confidential information, is extremely worrisome. The seemingly cavalier attitude toward security displayed in this case is deeply concerning.
The incident also raises questions about oversight and accountability. Who is responsible for this egregious lapse in security? Were appropriate security reviews conducted before the website’s launch? What steps are being taken to rectify this situation and prevent similar incidents from occurring in the future? The lack of immediate public response and explanation from relevant authorities only adds to the growing concern.
Furthermore, the location of the backend servers for this .gov site, seemingly in Singapore, adds another layer of complexity and concern. This unconventional hosting arrangement raises significant questions about transparency and potentially, compliance with regulations. The use of non-government servers for a website ostensibly related to government operations is highly unusual and points to a potential lack of adherence to standard procedures. The implications are far-reaching and require immediate attention from those responsible for governmental oversight.
This entire situation is nothing short of a debacle. The sheer negligence in security protocols is appalling. The potential consequences are far-reaching, and the lack of transparency surrounding the incident compounds the problem. Beyond the immediate technical fixes needed, a complete overhaul of security protocols and an investigation into how such a catastrophic failure occurred are absolutely essential. The entire episode underscores a critical need for enhanced cybersecurity measures and a greater emphasis on accountability within government agencies. This incident should serve as a stark warning about the dangers of neglecting cybersecurity and the importance of rigorous security practices in the digital age.